PUBLIC KEY INFRASTRUCTURE
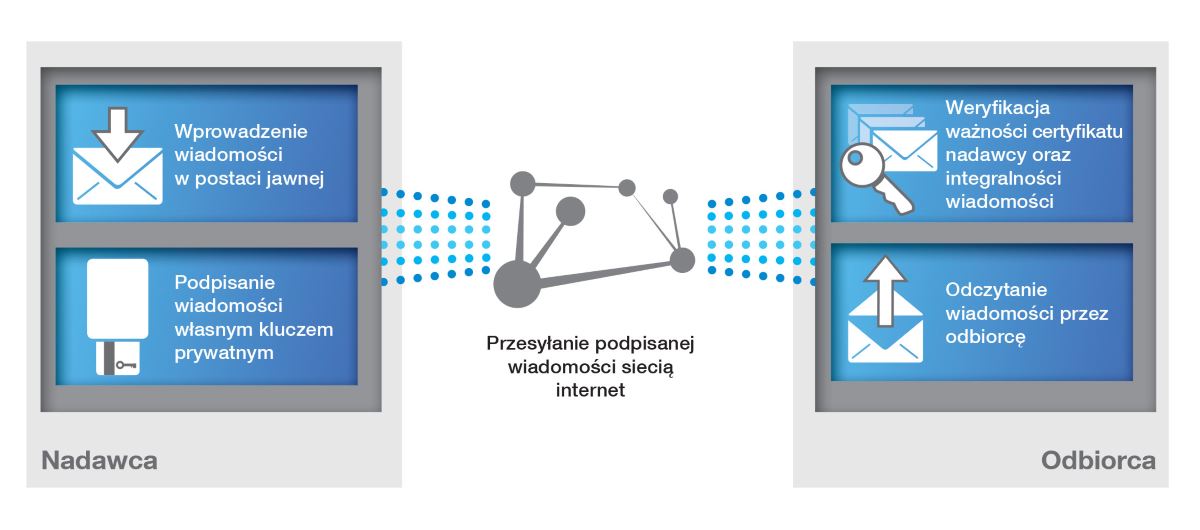
PKI is a system of secure electronic information exchange. It ensures the integrity, confidentiality and non-repudiation of content in electronic communication. By using PKI, e-mail user for ex. has guaranteed the authenticity of the sender and the integrity of transmitted data, as well as protection against unauthorized access.
To raise the level of information security in state institutions, local authorities, financial institutions, companies and enterprises Enigma for more than 20 years offers its own solutions to the construction and operation of PKI systems, such as:
MODUL-BASED PKI PLATFORM
Centaur Platform is a family of products, developed to bring organizations scalable, high technology, secure environment based on Public Key Infrastructure systems. All components of this environment were developed by Enigma SOI for more than 20 years, to implement newest cryptographic technologies and most convenient user experience on the market.
From the individual software modules you can build systems of generation, distribution and cancellation of public keys, differing in functionality, security levels and implementation costs. CENTAUR provides support for both small customers as well as systems for hundreds of thousands of users.
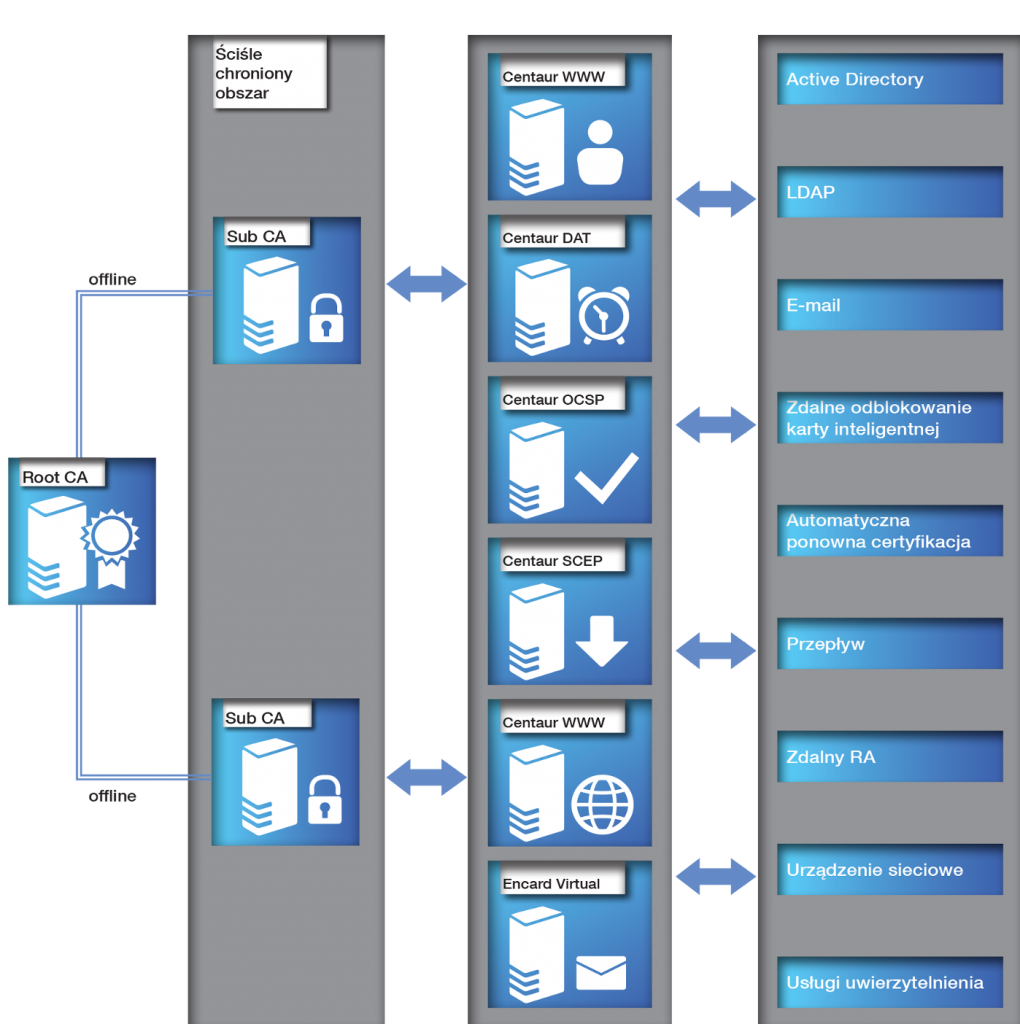
Centaur platform runs on the most popular and highly secured equipment to store cryptographic keys of Certification Authorities and users. It allows to create any number of Certification Authorities (CA), with a complex structure and hierarchy.
The main idea that stands behind our products is to give you products that will be as easy to use as it is possible – keeping in mind the highest security that is achievable. To do so we prepared
advanced functionalities providing users all the capabilities of electronic monitoring – document and e-mail signing, encryption and decryption of data, electronic sign verification etc. – with an interface as simple as possible. Users do not have to remember to recertificate. Users do not have to worry about data encrypted with old keys – we will provide them with it in the background. Users do not have to seek for others user key – we will prepare it for them. Desktop or mobile – you choose – we will give you solutions to use PKI on every platform you need.
BENEFITS
- Protection of sensitive data confidentiality;
- User access control for systems and applications;
- Ensuring compliance with legal requirements, including Act on the Protection of Personal Data.
MODULES
Centaur CCK is the base module of the CENTAUR system. Responsible for the implementation of all key functionalities such as: configuration and parameterization, life management of keys and certificates, coordinating the cooperation of all modules of the system and collection and sharing of relevant information. The user friendly (native) GUI, will allow you to define distinct roles: operator, administrator, and System Security Officer. All persons performing their tasks in the system are identified with strong authentication methods based on encryption keys and certificates stored on smart cards. High security is a distinctive feature of the Centaur solutions. All configuration tasks can be performed only with the console running on the same computer on which the software is installed, which also (besides strong authentication) reduces the risks associated with unauthorized access.
Centaur PR is an easy-to-use application that supports users of Registration Authority. With it, you can perform tasks, such as:
- register a new user,
- key generation for user,
- create user certificate based on: delivered public key or key generated in the Registration Authority,
- export certificates and CRLs,
- revocation of user certificate,
- process users information in batch mode,
- graphic personalization of smart cards,
- prints to support the certification process (handover / acceptance of PIN, secure envelopes etc.),
- reports.
Centaur OCSP is a module that allows you to verify the certificate status on-line via the communication protocol described in RCF 2560. The OCSP is used to provide information on the current status of a given certificate, ie. whether the certificate is valid, revoked or suspended.
Centaur DAT is a module for generating timestamps confirming the existence of a document at a time. Generating timestamps is an important safety element. The system works with real-time clock, it guarantees the correct and accurate time stamping of documents.
The software performs the following tasks:
- acceptance of requests from users to issue a timestamp,
- verifies demands in terms of: syntactic correctness and user permissions to receive a timestamp,
- create timestamps if the request was accepted.
Centaur SCEP is an application that supports the certification requests from network devices which use SCEP. The application can work in automatic mode – allows for automatic or manual certification device, which requires the presence of an operator.
Centaur WWW software is a service provided through the Internet. It allows automatic re-certification (extension of the validity of the certificate within its validity period) of users who use smart cards.
SOFTWARE TOOL FOR THE IMPLEMENTATION OF PKI FUNCTIONS
PEM-HEART software is used in Public Key Infrastructure for the implementation of electronic signatures, cryptographic protection of electronic documents, including content via e-mail and the data on the disks. It could be used with certificates issued by standard or qualified Certification Authorities. PEM-HEART offers a standard set of functions for securing messages using cryptography, by supporting protection of message integrity, authentication, non-repudiation of origin of the author and confidentiality. It also verifies the signatures issued by qualified Certification Authorities.
BENEFITS
- Modern, safe and convenient way to sign documents (electronic files)
- Confirmation of the credibility of the sender (Identity-based cryptography)
- Guarantee data integrity and confidentiality
- Easy verification of the changes in signed documents
MODULES
Accessible through the Web and designed for the remote exchange of keys and certificates located on cryptographic cards PKCS#11 and in the files PKCS#12 (* .pfx, * p12). It is widely used to integrate with web systems that consumes PKI services.
Offers high-level functions of secure message (lock/unlock message), allowing very easy enable security mechanisms for any application created by the developers team. It is used to give developers all the PKI features with simple programming interface to integrate it within their products.
Clients software for data encryption, signing and verification of qualified electronic signatures for all electronic documents – works on Windows family system, Linux and MacOS. It integrates with the system to provide users with an easy way to use all the PKI possibilities.
A simple way to solve the problem of lost keys – in cooperation with Centaur CCK key archive. When the user needs to use one of his previous keys (to read e-mails encrypted with key that was lost in the past) our software will communicate to the archive, authenticate with current key and download the old private key – without any interaction with the user – everything in the background to provide user with information he needs.
SECURE E-MAIL SYSTEM
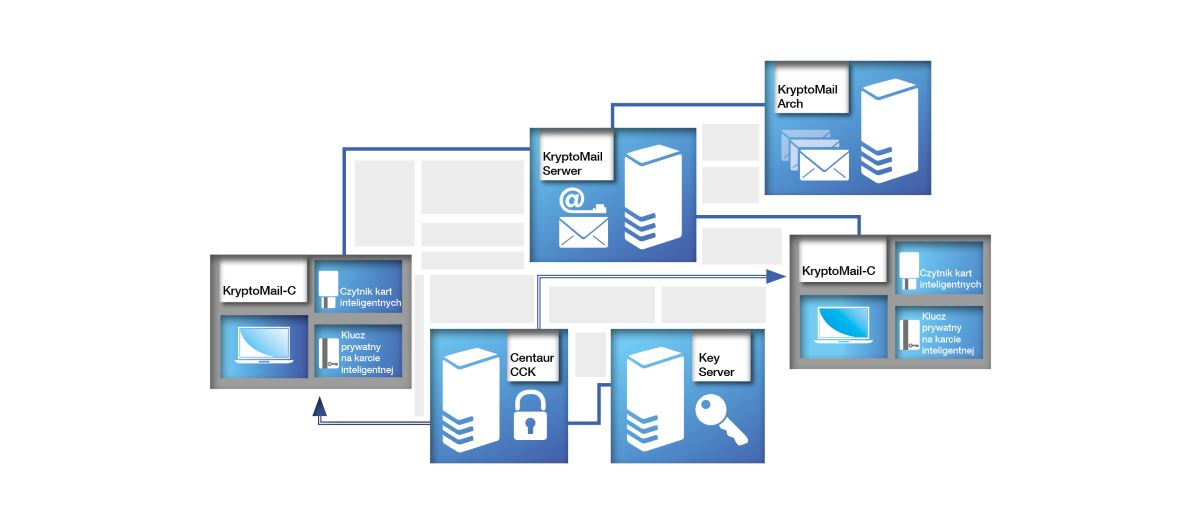
KryptoMail secure e-mail system is a modular software suite that protects the confidentiality and authenticity of the information transmitted in the electronic e-mail system, which uses strong cryptography. Electronic signature usage ensures the integrity and authenticity of all information, as well as the unambiguously verification of the sender identity. Only the sender and included recipients can read the message. E-mail protection is implemented in a way that does not require changing the habits of the user. Depending on the level of security, secures the system using password or microprocessor card. The system works with both desktop computers and mobile devices (including smartphones), and can be implemented in all organizations regardless of size.
BENEFITS
- Confirmation of the authenticity of the sender and the recipient in electronic correspondence
- Quick and secure way to transfer important information
- Protection against unauthorized reading and usage
- Protection against electronic attacks and spam
MODULES
Software for the end-users, used to encrypt and sign e-mails.
Moreover:
- cooperates with email archive and keys archive,
- supports all popular protocols, including SMTP, POP3 and IMAP (with the secure connections protected via SSLv3/TLS protocol),
- allows definition of address books stored in the LDAP,
- enables default sign and encryption of all electronic correspondence,
- has advanced filters to search information, including virtual folders and tags,
- smart protection against spam and phishing.
Mail servers software.
Allows:
- building complete mail server,
- user information is stored in LDAP repository (assigned to user aliases, mailbox size limits),
- uses strong authentication of users,
- based on certificate (rather than the most commonly used pairs username:password),
- allows the user to set automatic responses (autoresponders) at a time when the user is outside of the office,
- works with any client programs supporting SMTP, POP3 or IMAP.
Software allowing to build e-mail archive system:
- handles plain and confidential e-mails,
- allows building e-mail archive system,
- creates an index of the messages and lets them search based on: the sender, recipient, subject or date,
- all messages sent to the server go automatically to the archive,
- information on the identity of the sender, using electronic signatures with the messages are also gathered,
- ensures constancy and integrity of each stored message.
QUALIFIED ELECTRONIC SIGNATURE
A tool for the implementation of the advanced features of a secure electronic signature in the Public Key Infrastructure is PEM-HEART Siganture software.
The software allows the submission and verification of electronic signatures for qualified certification centers. PEM-HEART offers a standard set of cryptographic services to protect messages, ie. Protecting the integrity of the message’s authentication and non-repudiation of origin provided through a secure electronic signature and confidentiality. Verifies the signatures issued by all the qualified certification centers.
BENEFITS
- Modern, safe and convenient way to sign documents (electronic files)
- Sender statement of assurance (identification)
- Guarantee of data integrity and confidentiality
- Easy verification of the changes in signed documents