MOBILE SECURITY
In the days when access to mobile services surrounds us, the full safety of information sent with the use of such services becomes more and more significant. Today, laptops, tablets and mobile phones are tools, by means of which we make payments, take out loans, use medical services or company documents. In each of the above-mentioned situation we use sensitive data, the leakage of which may have serious consequences – both in the context of a specific person and the whole organisations. Therefore, the Enigma’s portfolio includes products ensuring mobile safety – allowing to take advantage of modern technologies at each place without fear.
SAFE NOTEBOOK
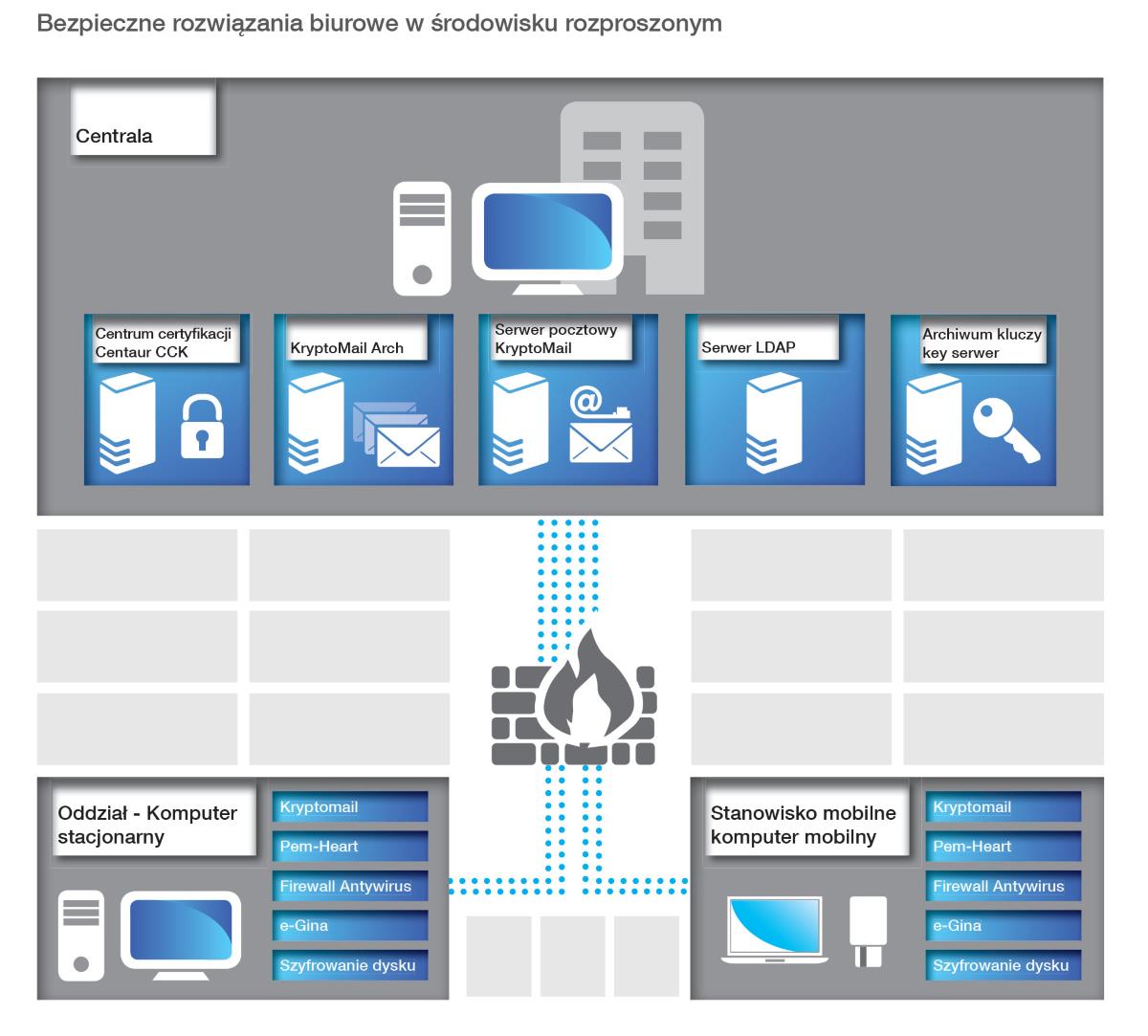
Recently, we may notice certain evolution of needs in relation to IT equipment. On the one hand, the demand for more mobile and visually attractive devices among employees grows. On the other hand, the company’s IT departments primarily want devices to be safe. Therefore, we have created a comprehensive system of protection of portable and desktop computers which allows safe office work in a dispersed environment. The solution makes it possible to create two separate work environments with classified information on a computer, each of them with a different safety level – e.g. classified and restricted information. A set of carefully selected protection technologies allows the system accreditation by appropriate services. One of environments is used for daily office work, the other is dedicated to access to classified systems and work with protected data.
BENEFITS
- safety of data gathered in portable devices
- use of the encrypted electronic mail
- possibility to work in two modes of access to restricted or non-classified information
- use of anti-virus and anti-spam protection solutions
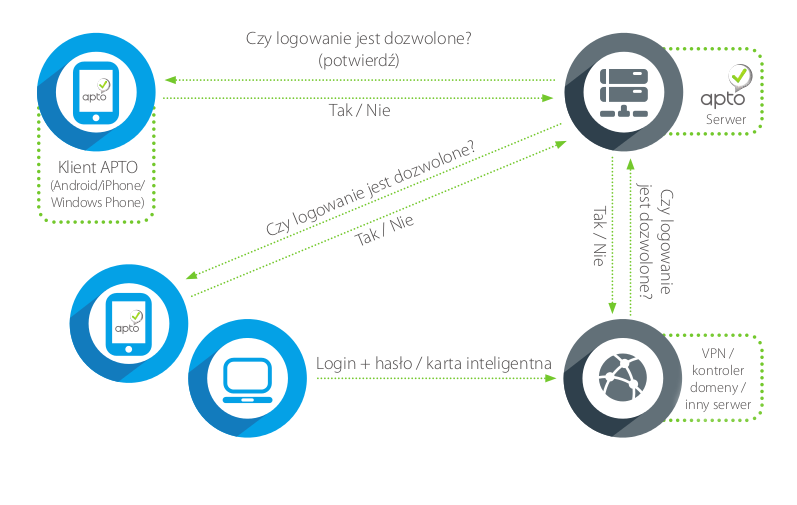
APTO – TWO-CHANNEL AUTHENTICATION SYSTEM
APTO is an innovative platform of authentication and authorization, combining ease of use with high security, based on the two-channel model of authentication mechanisms, mobile operating systems and PKI technology.
APTO is a program installed on the mobile device and is used to confirm any, outsourced operations. By using PKI it is fully secure and resistant even to sophisticated attacks. Prevents unauthorized access to protected resources. At the same time easily integrates with other systems and applications operating in the company. It replaces cumbersome and expensive to maintain, and, until recently, the most popular methods of user verification. It surpasses existing solutions in terms of safety and reliability. Moreover, clear interface provides intuitive operation. The two-channel mechanism to confirm (“something you have + something you know”) is the best way to improve the safety of operations, next to high-technology PKI. The user has the opportunity to refuse the operation if it raises his suspicions. Increasingly frequent incidents of man-in-the-middle theft, phishing and attacks using spyware software are also eliminated. Even highly advanced attacks are not dangerous for the security of information, through the use of encryption, among others.
BENEFITS
- prevents unauthorised access
- uses a two-factor transaction authorisation mechanism
- enables work with the solutions of different vendors
- provides two-factor authentication to enterprise applications
EGINA MOBILE – LOCAL MOBILE AUTHENTICATION SYSTEM
eGINA Mobile is a software allowing to log on to the Windows Mobile system by a user with the use of crypto-processor cards and the PKI technologies as an authentication mechanism for mobile devices.
The system eliminates the problem of weak, rarely changed passwords. It may be used both on computers disconnected from the domain controller as well as those which are members of the Windows domain. The implementation of the software requires the possession of the PKI infrastructure from which cards, keys and certificates will come.
BENEFITS
- makes it possible to authenticate a user and unblock access to devices and resources,
- joins the logging process with the possession of a cryptographic card,
- uses short and easy to remember PIN passwords,
- automatically blocks a station after removing a card,
- in terms of equipment it protects a station against unauthorised access.



