DATA SECURITY
The free flow of information in ICT networks of enterprises and the high availability of many resources favour various type of threats. The lack of appropriate safety policy and appropriate safeguards frequently results in serious consequences, including the loss of data and resources, decrease in work efficiency, huge material losses.
The solutions of Enigma protect enterprise information, minimise threats, monitor and react to incidents of network safety inside and outside an organisation.
The solutions of Enigma protect enterprise information, minimise threats, monitor and react to incidents of network safety inside and outside an organisation.
ARCHIVING OF DIGITAL DOCUMENTS
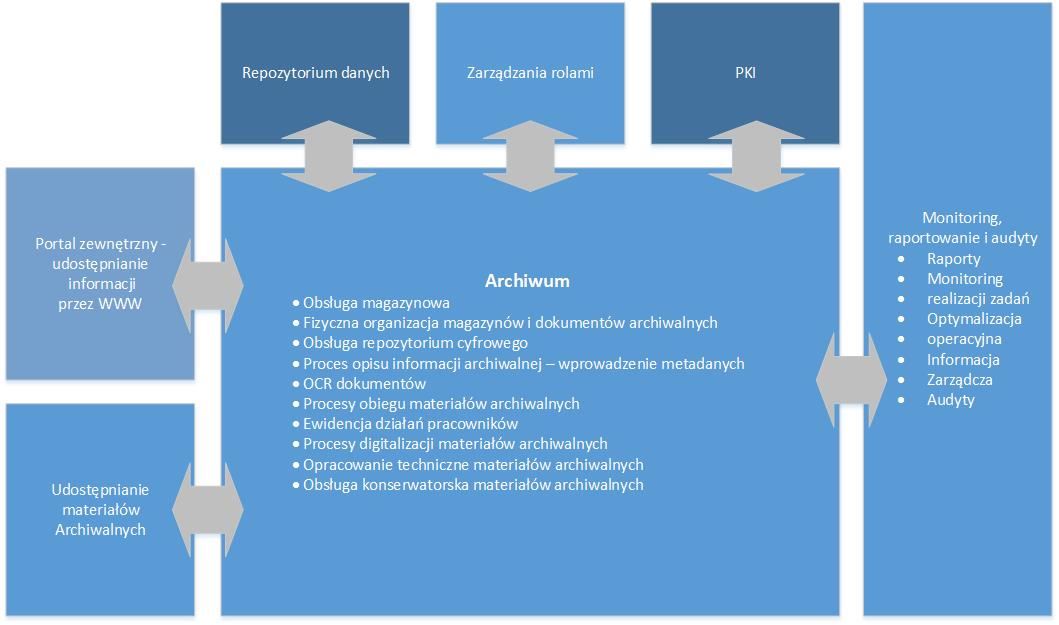
The Digital Archive System allows to comprehensively manage documents in each form – pictures of documents (scanned paper documents), electronic documents (text files, electronic mail, multimedia), paper documents, and their flow within an organisation.
The system allows for the storage – in a repository – of various types of archival documentation and its multi-level description:
- File documentation.
- Photos.
- Audio documentation.
- Video documentation.
- File records, archival aids.
- Cartographic materials.
- Normative acts.
- Digital documents.
The system makes it possible to record and group documents into groups, series/subseries and to classify them as single objects. Due to its internal architecture, it makes it possible to create an association between documents and stored objects. Entitlements in the system are based on roles, which makes it possible to flexibly create entitlements. Depending on entitlements, a user’s interface – which displays options available for a person having certain entitlements – is dynamically changed.
Due to the implementation of PKI, it guarantees the safety and invariability of the stored and shared archival documents and the full accountability of employees.
LEGAL FRAMEWORK OF THE SYSTEM
The Digital Archive System is consistent with the following orders and norms:
- Act of 14 July 1983 on the National Archival Resource and Archives.
- Order No. 13 of the Central Directorate of State Archives of 29 June 2011 on digitisation.
- Order No. 4 of the Central Directorate of State Archives of 1 February 2013 on the organisation of making archival materials available in the state archives.
- Decision No. 3 of the Chief Director of State Archives of 10 January 2007 on the safeguarding and protection of the archival resource of the state archives.
- ISAD(G) – General International Standard Archival Description.
ISAAR – International Standard Archival Authority Record of corporate bodies, persons and families, used for the standardised description of an entity generating and gathering files, strictly related to the ISAD standard.
EXEMPLARY MODULES OF THE SYSTEM
The modular structure of the Digital Archive System allows high flexibility and possibility of adaptation to the volume of resources.
- SEARCH
- DESCRIPTION OF AN ARCHIVAL UNIT
- MODULE OF ACQUISITIONS AND WITHDRAWALS
- WAREHOUSE MODULE
- CONSERVATION ACTIVITIES
It possesses an advanced search of information on the stored archival materials. The search uses metadata introduced in the process of description of archival materials, as well as other information e.g. in the form of OCR text or additional descriptions of archival units.
Basic features of the search module include:
- Searching depending on the profile and entitlements of a user.
- Searching of information using many search questionnaires e.g. topic-based/subject query, personal query, ranges of reference numbers, structural browser.
- Searching of descriptions related to archival units.
- Searching of descriptions of files.
- Searching in a personal index.
- Access to context data (group, subgroup, series, subseries) from the level of a description of an archival unit and through a structural browser.
- Searching of issues, cases, problems mentioned in archival materials, as part of a topic-based/subject query.
- Searching of persons listed in a personal index, as part of a personal query.
- Searching of a topic-based/subject query in two ranges: simple and advanced searching.
- A search which makes it possible to create model files allowing to search information related to a basic entry (e.g. Polish Pope, it will also find Karol Wojtyła, John Paul II, JPII).
- Searching in the scope of a location field is supported by a model file of geographical names.
The archival unit description module is introduced by users or through automatic mechanisms. Due to the key importance of information introduced at that stage, the system possesses mechanisms related to the control of the introduced data. The process of verification of work and introduced data is used as part of the system. Due to such solution it is possible to transfer knowledge from employees verifying data to employees introducing data, and the introduced data is of high quality.
Basic features of the archival unit description module in the Digital Archive system include:
- Introduction of a description of an archival unit, audio materials, photos and video materials.
- Introduction of descriptions of files and record aids.
- ODescription consistent with ISAD(G), ISAAR and rules accepted by the Central Directorate of State Archives and Polish law.
- Use of multi-level dictionaries (possibility of adding and editing dictionaries depending on the possessed entitlements for local and global dictionaries).
- Description at the level of a personal index.
- Possibility of data export (e.g. public archival inventory).
- Reporting of activities related to an archival description and the amount of information introduced by the system users.
A module of acquisitions and withdrawals makes it possible to record the received and withdrawn archival materials in an organisation. Archival materials may be received in various forms – in a paper and electronic form.
Basic features of the module include:
Recording of accessions
- Register of transfer and receipt lists (book of acquisitions)
- Registration of inclusions in the form of inflow, purchase, gift, deposit
Recording of exclusions
- Withdrawal is registered when there is a record in the book of acquisitions or in the register of groups or archival collections.
- The system automatically numbers withdrawals (creates a book of withdrawals).
- Register of withdrawals (book of withdrawals).
The warehouse service module makes it possible to fully monitor warehouse management. It makes it possible to define warehouses, warehouse space, rack, stockbook, shelf, drawer, item etc. It allows to automatically assign values to a topographic inventory which indicate the place of storage of archival units in archival warehouses, for a number of archive reference numbers, according to a recording order of transfer and receipt lists or archival groups (collections).
As part of the module it is possible to prepare a number of reports, including:
- List of determiners of a topographical inventory for the indicated string of reference numbers.
- List of strings of reference numbers stored in individual archive rooms.
- List of free warehouse space in individual archive rooms.
The module of conservation activities makes it possible to:
- Create, edit and remove descriptions of conservation activities for individual archival reference numbers.
- Prepare statistical registers picturing the specification of conservation activities for individual strings of reference numbers and archival warehouses.
- Determination, editing and removal of information related to climate parameters of rooms in which archival materials are stored.
- Possibility to introduce conservation recommendations for each archival unit.
- Registration of activities involving sterilisation and disinfection of documents.
SAFE ELECTRONIC MAIL
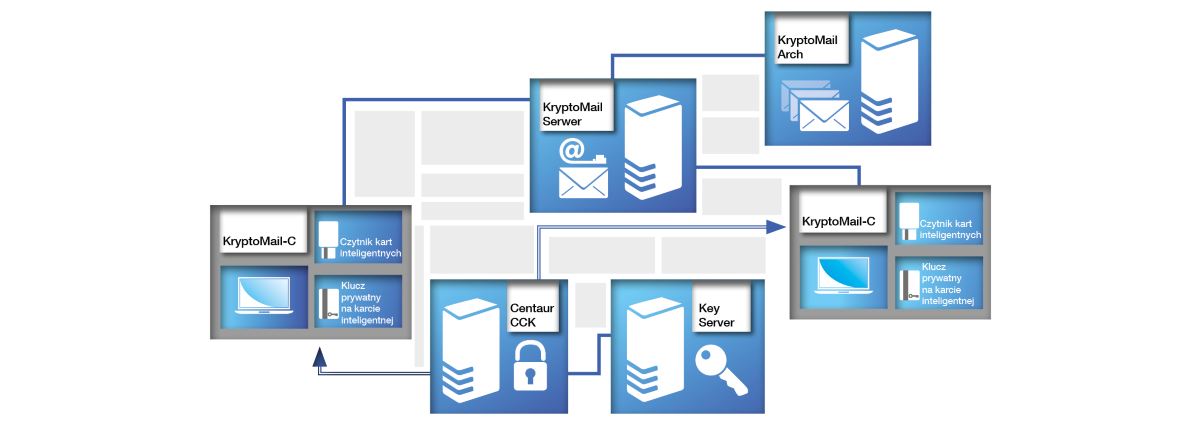
The safe electronic mail system – KryptoMail is a modular software package used to protect the confidentiality and authenticity of information sent in the electronic mail system which uses strong cryptographic mechanisms. Using the electronic signature function allows to obtain the integrity and authenticity of all information, as well as to unambiguously verify the sender’s identity. Due to it, only the sender and the indicated recipients have access to the content of a message. Implementation of the electronic mail protection takes place without changing the habits of a user. Depending on the required level of safety, the system is protected by a password or microchip card. The system works both on desktop computers and mobile devices (including smartphones) and may be installed in all organisations, regardless of their size.
BENEFITS
- confirmation of the authenticity of a sender and a recipient in electronic correspondence
- quick and safe method of the provision of important information
- protection against unauthorised readout and use
- protection against electronic attacks and spam
INDEPENDENT MODULES OF THE SYSTEM
- software for end users;
- used to encrypt and sign e-mail messages;
- cooperates with the archive of e-mails and keys;
- supports all popular protocols, including SMTP, POP3 and IMPA (with a possibility to protect connections with the SSLv3/TLS protocol);
- allows to define address books stored in LDAP;
- allows to sign by default and encrypt the entire electronic correspondence;
- includes advanced information search filters, including virtual folders and tags;
- intelligent protection against spam and phishing.
- software for the support of electronic mail servers;
- allows to build a complete mail server;
- data of users is stored in the LDAP repository (assignment of aliases and limits of the size of mailboxes to users);
- strong authentication of users based on a certificate (assignment of aliases and limits of the size of mailboxes to users);
- allows a user to set automatic responses (the so-called autoresponders) when a user is outside the office;
- cooperates with any client programmes supporting SMTP, POP3 or IMAP protocols.
- supports ordinary and confidential messages;
- allows to create e-mail archiving systems;
- creates indices of messages and allows to search across them based on the following criteria: sender, recipient, subject or date;
- all messages sent to the server are automatically added to an archive;
- stores information on the sender’s identity using electronic signatures in messages;
- ensures the continuity and integrity of all messages stored.
SAFE DOCUMENT CIRCULATION SYSTEM WITH THE CONFIDENTIALITY CLAUSE
A secret office within general meaning is a place where documents containing classified information with various clauses of secrecy are received, registered, stored, sent or released to authorised persons. A secret office is a basic element of safety of an organisation, company or corporation implementing strictly defined, very specific tasks related to the processing of classified information.
The Secret E-Office (E-Kancelaria Tajna) system developed by Enigma, constituting an extensive IT system, fulfils all functions of a classic secret office and, at the same time, improves the process of registration, distribution and storage of classified information, ensuring the required level of its safety. The system is not only limited to electronic recording and printout of documents or ensuring their traditional circulation in an organisation unit, but it is also safe electronic exchange of classified documents between many offices, e.g. between company’s headquarters and its regional branches – using safe and encrypted network connections.
BENEFITS
- accelerated distribution and access to documents containing classified information
- simple office services related to the registration and storage of documents
- circulation of documents in a paper form limited to the minimum
- reduction of costs in the scope of handling of classified information due to the exchange of documents using a safe electronic mail
LEGAL FRAMEWORK OF THE SYSTEM
- Act of 5 August 2010 on the Protection of Classified Information (Journal of Laws, No. 182, item 1228 of 2010)
- Regulation on the organisation and functioning of secret offices (Journal of Laws of 2013, No. 0, item 11)
- Regulation on the method for marking of materials and placing of confidentiality clauses on them (Journal of Laws of 2011, No. 288 item 1692.)
- Regulation to the Act on Archives:
- on necessary elements of a structure of electronic documents (Journal of Laws 06.206.1517)
- on a detailed method of electronic document handling (Journal of Laws 06.206.1518)
- on technical requirements for formats of saving and IT data carriers on which archival materials have been recorded and provided to the state archives (Journal of Laws 06.206.1519)
- Regulation on basic requirements for ICT safety (Journal of Laws 05.171.1433)
- Regulation on the office instructions, uniform subject file index and instructions on the organisation and the scope of operation of in-house archives (Journal of Laws of 2011, No. 14, item 67)
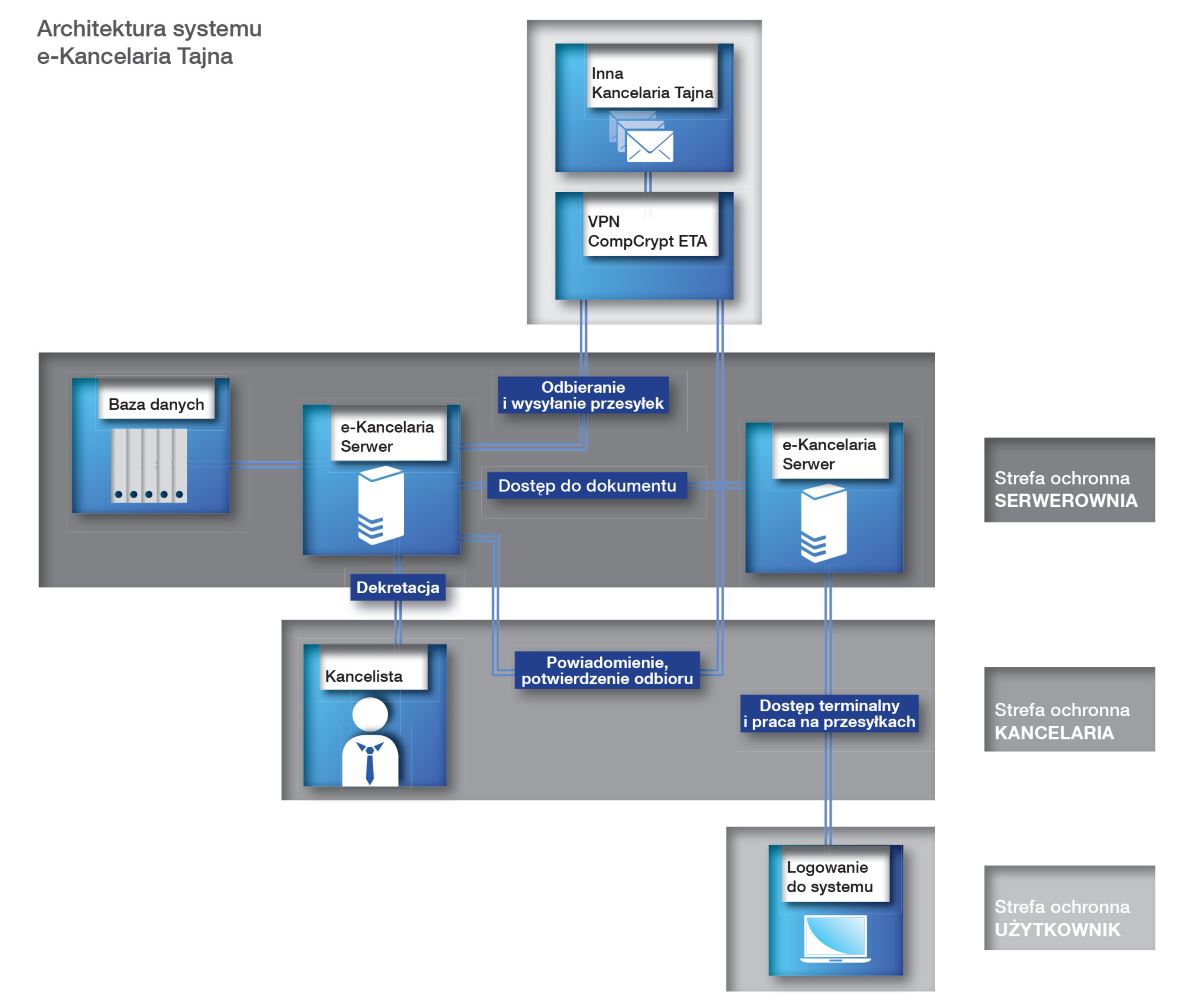
MODULES OF THE SYSTEM
A user logs on to the system using a Certificate issued by the Certification Centre. Using an access application after identification, authentication and verification of the level of entitlements, a user obtains access to documents. All documents are signed with the use of a qualified certificate and automatically provided for registration in an office.
After authentication with a qualified certificate using the “e-office Clerk” (“e-kancelaria Kancelista”), a clerk obtains access to the management of logs, registers, establishment of files, sharing of documents.
The e-office server plays the role of the “system core” responsible for the storage and control of access to classified documents. The submitted documents are protected against unauthorised access of third parties.
A very important element of the system safety is the control of access to documents containing classified information with the use of cryptographic cards and PKI infrastructure. The whole exchange of correspondence in the office takes place with the use of encryption devices – CompCrypt ETA, having a cryptographic protection certificate issued by the Internal Safety Agency, allowing them to process classified information, including information with the “confidential” clauses.
SAFE GATHERING AND STORAGE OF LOGS
ProtLog is a system used for the safe gathering and storage of logs of applications and devices. Due to the use of cryptographic mechanisms of an electronic signature and time markers, the system ensures the possibility to detect and identify each introduced change by the verification of coherence of logs which have been archived with the source ones. It may support any number of sources and events of any form. ProtLog is a system intended for mission-critical applications. Individual components of the system have been structured in such a way so as to ensure the maximum level of availability and support the existing reliability increasing technologies.
PROTLOG SYSTEM FEATURES
- detection of modifications of any logged event/events
- detection of removal of an event/events, including the removal of the last logged records
- detection of “manual” addition of an event/events to the base, omitting the Prolog mechanisms
- high resistance to sabotage (e.g. power cut-off, ProtLog server killing)
- possibility to verify the cohesion by the authorised ITC safety inspector who possesses its own microchip card with a private key
- use of time markers in order to guarantee the correctness of the logged dates
DATABASE SYSTEMS – EGIDA
As interest in the processing of significant amount of telecommunications data, mail data and internet data grows, Enigma has created the e-Gida database system facilitating the viewing, processing and generating of reports from the acquired data.
EGIDA CONSTITUTES THE IT SOLUTION SUPPORTING STATE AGENCIES IN:
- registration of applications and results of applications for obtaining telecommunications, mail and internet data
- automatic preparation of reports related to telecommunications, mail and internet data:
- Register of applications for obtaining telecommunications, mail and internet data
- Detailed register of applications for obtaining telecommunications, mail and internet data
- Report for the Regional Court related to obtaining by an organisation of telecommunications, mail and internet data
EXEMPLARY MODULES OF THE SOLUTION:
- Database
- Report module – allowing users to:
- independently define reports on the basis of information from a database
- generate previously defined reports without user’s participation
- WWW interface – making available – in a safe manner – forms of applications for workstations (computers) working online in a safe computer network
- Module of the management of dictionaries used as part of the application
- Offline station support module: importing and exporting data
A complete set of data is processed by the central server.
The system is intended for the processing of classified information with the RESTRICTED clause.